In the previous tutorial we saw how to build a simple login page for Streamlit,in this post we will check out the various ways to secure our app and in most cases any web app that has a login and a form of database.
In designing your web applications there are certain measures to take to ensure that you reduce the level of vulnerability as much as possible.
The first steps is in restrict unauthorized and illegal access to essential aspect of the app. So in this case we can create a login/signup page.
And the second step is to secure the data by hashing or encryption or both.
But in most cases, if measures are not taken, our app can be attacked using the login section usually due to issues with our SQL (Structured Query Language) we use at the back-end.
Hence we have to secure our login from SQL injection.
So what is SQL Injection?
SQL Injection is the placement of carefully crafted malicious code in SQL statements via a web page input area. In most cases the code placed in the SQL statement are usually valid and logical additional input that will yield a result when executed.
For example
SELECT * FROM userstable WHERE userid = 5;
But if we add an additional query to our statement such as OR 1 =1, it will still make sense to the SQL engine behind the seen,hence it will execute as required and return ALL rows from the userstable.
SELECT * FROM userstable WHERE userid = 5 OR 1=1;
There are several carefully crafted queries that can be used to retrieve information from an SQL database. Hence it is recommended to follow the accepted standard – at least by following these you reduce the risk of being hacked or attacked.
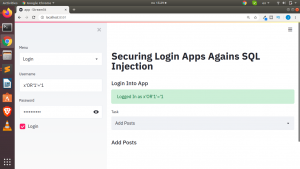
Let us see how to apply this concept to our Login Section we created.
First of all these are some format of writing SQL queries that we are NOT TO USE, although they work when used.
String Concatenation(using +): It is not recommended to use string concat with your SQL statements. This is very dangerous especially if you format a comma or character. It is not the best method
"SELECT * FROM userstable WHERE username = '" + username + "AND password= '" + password + "
or
"SELECT * FROM userstable WHERE username='" + username + "'AND password='" + password + "'";
String Format: This where you use the string.format() method or %s and you parse your input into the SQL statement. This too is not safe
"SELECT * FROM userstable WHERE username='{}' AND password = '{}'".format(username,password)
F-String: The new F string format also has the same vulnerability when used hence avoid it in certain statements.
f"SELECT * FROM userstable WHERE username= '{username}' AND password= '{password}'"
Inserting any of these code in our input will be a form of SQL Injection and will return a result.
x'OR'1'='1
admin' --
admin'/*
' or 1=1--
' or 1=1/*
' or 1=1#
admin' #
') or '1'='1--
') or ('1'='1--
For example using admin’ — within any of the above statement will result in something like this
"SELECT * FROM userstable WHERE username='{}' AND password = '{}'".format(username,password)
“SELECT * FROM userstable WHERE username=‘admin ‘–‘ AND password = ‘admin ‘–‘”
The reason is the ‘ being used will be seen as part of the SQL query and execute hence it is recommended to separate your string input from the SQL query statement to ensure that they are parsed well.
What is SAFE to USE
It is best and safer to use the ? in place of the other methods above. Using ? and a tuple that contains your values is safe and sure. This separate the string values from the user from the SQL statement.
'SELECT * FROM userstable WHERE username =? AND password = ?',(username,password)
You can also use %s but it must be with a tuple not a string format.
"SELECT * FROM userstable WHERE username= '%s' AND password='%s'",(username,password)
"SELECT * FROM userstable WHERE username= %s AND password= %s",(username,password)
These are some of the measures to secure our login section from SQL injections. You can also check out the OWASP Top 10 security measures for more ways to secure your web app.
After the login section/page is secured the next step is to ensure that the data in our database is also secured.
Hashing and Encryption
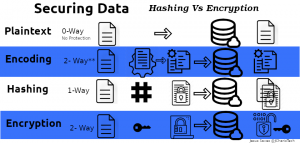
We secure the data in our database using either Hashing or Encryption or Both.
Hashing is usually useful for protecting passwords whiles Encryption is useful for details that we will need to view later on by another person or the same person such as bank details, user profiles, pin etc.
In another tutorial we will go in depth into the concept of Hashing vs Encryption vs Encoding.
You can check out the entire video tutorial here
Thank you for your time
Jesus Saves
By Jesse E.Agbe(JCharis)
