As a developer or data scientist or programmer that works with data, it is essential to know how to protect your data and keep it secure. In this tutorial we will learn about the various ways we can protect our data using python. We will be focusing specifically on protecting passwords.
In building a CRUD app that stores data in a database, it is required that you keep in view the best security practices to ensure that at least your DB is a bit secure. Remember there is no 100% security proof system- all we need is time,compute and know-how to attack and make vulnerable any ‘secure’ system.
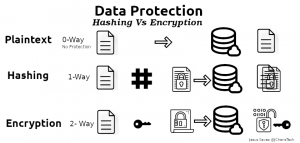
Let us see the various ways we store passwords in our database. The various ways include the following
- Plaintext
- Hashing
- Encryption
Using Plaintext
This is the easier but least safe method of storing important data such as passwords into a database. In this case there is no protection or encryption, the data is stored in plain text. Hence if someone get access to the database, he or she will be able to see the entire passwords.
This is not the best method and it is not recommended at all.
Using Hashing
Hashing is the transformation of data/string of characters into a fixed-length value that represent the same original data using a hash function. Normal hashing ensures that in every case it will generate the same hash value for the same data. This is quite useful when you want to check if the value are the same. But the downside is that is cannot be unhashed. Hence it is quite useful when working with passwords.
Hashing involves a one way functional approach to data protection. That means you cannot un-hash once you have hashed a plaintext.
The main purpose of hashing is to ensure data integrity and well as to verify data to make sure they are the same.
Moreover it is possible to know the value behind the hashed text by using the same hash function on several plaintext words. and then matching them if they are the same. This is what is know as rainbow cracking.
To solve this issue , there came the introduction of SALT hashing – which is where a unique random number is added to each plaintext before hashing. This makes it difficult to guess what the initial plaintext was even if you use the rainbow cracking method.
Examples of Hashing Algorithms
- Secure Hash Algorithm (SHA)
- SHA-1
- SHA-2
- sha2-224,sha2-256
- sha2-384,sha2-512
- Blake2
Examples of Hashing Libraries
- Hashlib
- Passlib
- Bcrypt
- Scrypt
Before we move on to encryption let us talk about encoding first.
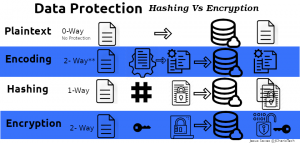
Encoding: Is the process of transforming data( in our case plaintext) to another format that can be easily and safely used by a different system.In encoding the scheme used to transform the data is not kept secret unlike encryption. Hence we can say that in encoding there is no private key or public key used,there is only a schema.
The main purpose of encoding is to protect the data integrity – ensuring that you get the same data in a different system or environment.
For example when transferring data as machine code (binary 1 and 0) it can be difficult to know if the data being sent are images or letters or the like. This is because the binary data is dependent on the type of data it represents hence we have to encode it to a better format that is suitable for the new or different environment.
Examples of encoding involves transforming Latin1 to ASCII(American Standard Code for Information Exchange) or text data to ASCII using Base64 encoding.
Using Encryption
Encryption is similar to encoding except that in encryption, the data(plaintext) is transformed to another format (usually called ciphertext) using a cipher function or key which can only be read by anyone with the key used to transform it. Hence encryption is a two way functional approach. We have the first way of hiding it using a cipher function and then the second way of using the cipher function/key to uncover it. This concept of un-hiding the ciphertext to get the initial plaintext is termed Decryption.
Encryption is better than storing your password as plaintext but the only issue is that if a person have the cipher function/key he can decrypt it to get the plaintext.
Encryption can be either symmetrical or asymmetrical types.
The main purpose of encryption is to secure data. Examples of encryption algorithms include
Examples of Encryption Algorithms
- AES
- RSA
Examples of Encryption Libraries
- Cryptography
- PyCrypto
- Tink
- Keyczar *
Difference Between Encoding and Encryption
Encoding and encryption may look similar but they are quite different. In encoding there function/algorithm used to transform the data into a different format is not a secret, it is usually public. But in encryption, there is a private and public key/secret to hide the data and uncover the ciphertext.
Now let us see how to implement these concept in code
Encryption
To recap encryption is plaintext to ciphertext. We will be using cryptography or pycrypto in our example
Installation
pip install cryptography
Let us start. We will be using a symmetric encryption algorithm.
from cryptography.fernet import Fernet
As we learnt we will have to create a secret key to be used to encrypt and decrypt our data.
secret_key = Fernet.generate_key() f = Fernet(secret_key) plain_text = "this is a plain text" cipher_text = f.encrypt(plain_text)cipher_text
Decrypting Our Ciphertext
f.decrypt(ciper_text)
Hashing Using Hashlib
As we learnt earlier there are several libraries we can use for hashing. We will be using hashlib and bcrypt in this tutorial. Hashlib normally can be found in your standard library if not you can install it with pip
Installation
pip install bcrypt passlib
Let us start
import hashlib
def make_hashes(password):
return hashlib.sha256(str.encode(password)).hexdigest()
def check_hashes(password,hashed_text):
if make_hashes(password) == hashed_text:
return hashed_text
return False
plain_text = "this is a plain text"
hashed_text = make_hashes(plain_text)
print(hashed_text)
Encoding
To recap encoding is simply plaintext to another format easy to be consumed by a different system.
We will be using Base64 to help us with that.
Base64 is a number system that shows how many different characters represent numbers and alphabet and in this case it has 64 characters.
26 Uppercase + 26 Lowercase + 10 number/digit = 64 characters
A simple example of encoding is like converting text to ASCII.
"this is plain text".encode('ASCII')b'this is plain text'
Base64 Encoding
import base64 b64_bytes = base64.b64encode(b'this is a plain text') b'dGhpcyBpcyBhIHBsYWluIHRleHQ='
Base64 Decoding
encoded_text = b'dGhpcyBpcyBhIHBsYWluIHRleHQ='. base64.b64decode(encoded_text) b'this is a plain text'
We have seen the various ways we can secure our data as well as protect data especially passwords. We now have understood the difference between encoding,hashing and encryption using python.
You can check out the video tutorial below
Thank you for your time
Jesus saves
By Jesse E.Agbe(JCharis)